In early 2024, a massive cybersecurity campaign known as EmeraldWhale exposed over 10,000 private Git repositories, leaking more than 15,000 cloud service credentials. Attackers exploited misconfigured Git repositories, gaining unauthorized access to sensitive data stored in plaintext. This breach underscores a critical and recurring issue: hardcoded credentials, mismanaged secrets, and inadequate security controls remain among the top attack vectors in enterprise environments.
As enterprises embrace multi-cloud strategies and modern application architectures, the complexity of securing sensitive data, managing machine identities, and implementing encryption services has grown exponentially. Yet, many organizations still rely on outdated security practices. Static secrets stored in configuration files, manually rotated certificates, and ad-hoc encryption implementations introduce significant security risks—both in terms of data breaches and compliance violations.
At ICT.technology, we've observed that organizations often underestimate these risks until they experience a security incident. Securing modern infrastructure requires more than just technology—it demands a holistic, automated approach that ensures scalability, compliance, and operational efficiency. This is where HashiCorp Vault comes in.
Vault has emerged as the industry standard for enterprise security infrastructure, providing a unified solution for secrets management, identity-based security, and encryption-as-a-service. Instead of simply storing secrets, Vault dynamically generates them, manages machine identities, and automates encryption, all while enforcing fine-grained access controls.
In this article, we’ll explore how Vault transforms security infrastructure, why traditional approaches fall short, and how enterprises can leverage Vault to enhance their security posture. Whether you’re a decision-maker evaluating enterprise security solutions or an engineer looking for a scalable way to manage secrets, this guide will provide a practical roadmap to securing modern infrastructure with HashiCorp Vault.
Why Traditional Security Fails and Why Vault is Different
Traditional approaches to security infrastructure, which often relied on static credentials, manual certificate management, and disparate encryption solutions, have proven inadequate for modern enterprise environments. These methods frequently lead to security vulnerabilities, operational inefficiencies, and compliance challenges.
Imagine a typical enterprise environment: applications, services, and infrastructure components need to authenticate, access sensitive resources, and protect confidential data. Traditionally, this has been handled through a patchwork of static credentials, manually configured encryption keys, and separate certificate management tools. Perhaps TLS certificates are acquired manually from an external certificate vendor, a process that can easily take days to complete.
The problem? These approaches are neither scalable nor secure. Static credentials are hardcoded in source code or configuration files, making them vulnerable to leaks. Manually rotated keys introduce human error and operational bottlenecks. Disparate security solutions increase management complexity and compliance risks. TLS certificates often have extremely long time-to-live (TTL) values to reduce manual overhead, further exposing organizations to security risks.
But there is no reason organizations should accept this as the status quo. Vault redefines security infrastructure by introducing a unified, automated, and identity-based approach to secrets management, machine authentication, and encryption services. Instead of just storing secrets, Vault generates them dynamically, enforces fine-grained access control, and automates key lifecycle management.
With Vault, enterprises can replace scattered security workflows with a centralized platform that seamlessly integrates with their infrastructure—whether on-premise, in the cloud, or across multi-cloud environments.
This approach fundamentally changes how organizations handle security infrastructure. Instead of managing disparate security systems, organizations can implement a unified platform that handles everything from machine authentication to encryption services.
Consider a typical enterprise scenario where applications and services require secure communication, access to sensitive resources, and encryption capabilities. With traditional approaches, managing these requirements would involve multiple specialized systems, each with its own management overhead and security considerations. Vault simplifies this by providing centralized security services through its unified API.
However, implementing proper security infrastructure requires careful consideration of enterprise requirements. Organizations must not only enable sophisticated use cases like PKI management and Encryption-as-a-Service, but also design their Vault architecture to support high availability, disaster recovery, and compliance requirements.
At ICT.technology, we implement Vault through a comprehensive, modular, and best-practice architecture that addresses enterprise needs.
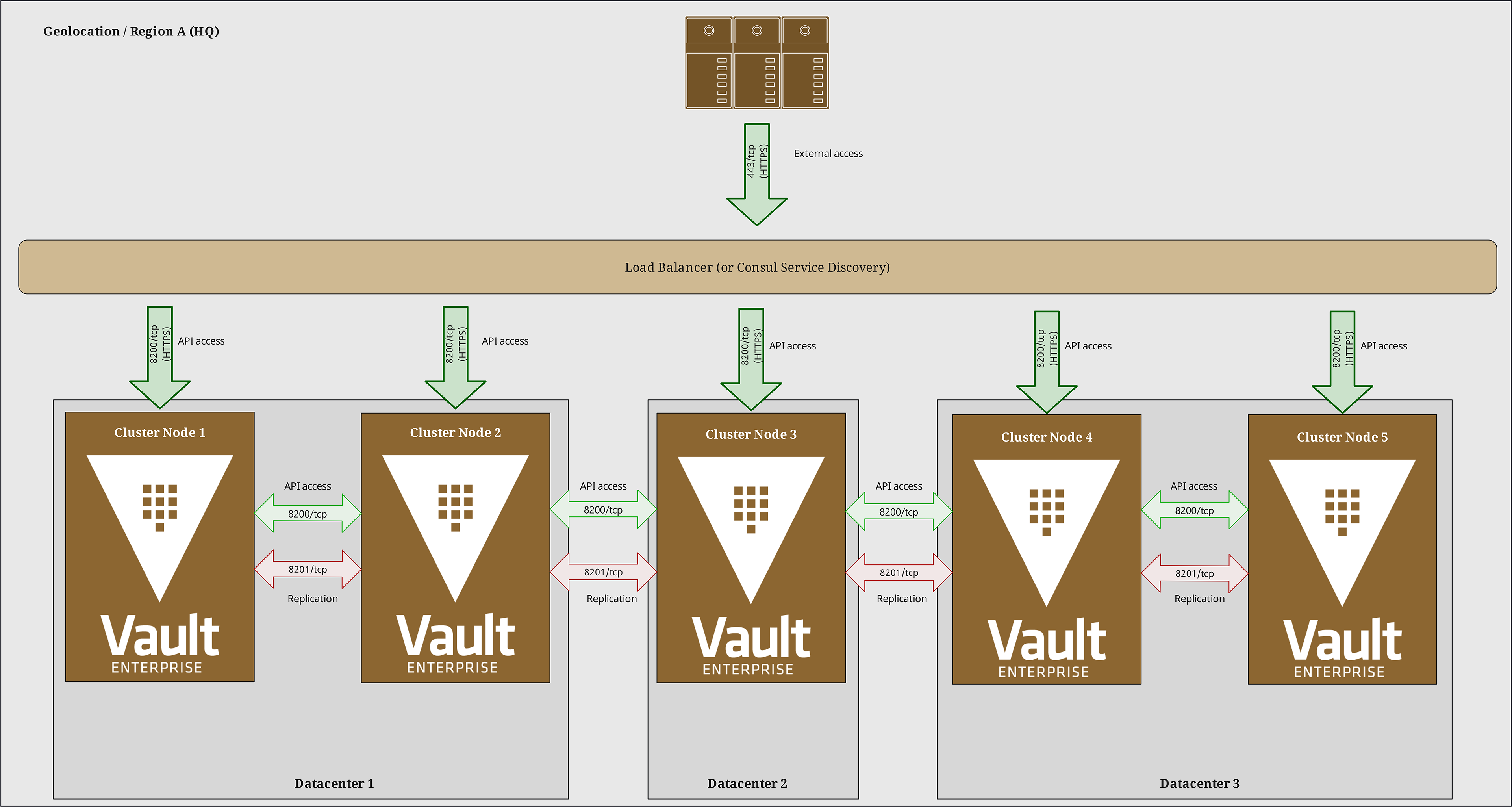
The foundation consists of a highly available Vault cluster, which is typically deployed across multiple datacenters, if possible, or at least different fault domains. This ensures that no single point of failure can take down an entire cluster at once.
Using Vault's integrated Raft storage backend, which provides resilience and consistency for enterprise deployments, data is synchronized between cluster nodes and even across entire clusters. Performance Replication and Disaster Recovery clusters ensure business continuity and meet regional data sovereignty requirements, such as GDPR compliance for EU customers.
Hardware Security Modules (HSMs) provide additional protection for master keys and critical secrets, meeting stringent compliance requirements for industries such as finance and healthcare.
Identity-Based Security for Humans and Machines
 The true strength of Vault becomes apparent when examining its sophisticated approach to identity-based security. In modern enterprises, managing identities extends far beyond human users to include services, applications, and infrastructure components. For instance, Starbucks utilizes HashiCorp Vault to secure secrets and manage identities for over 100,000 edge devices across its retail locations. This implementation ensures that both human and machine actors are authenticated and authorized securely, highlighting Vault's capability to handle complex identity-based security requirements.
The true strength of Vault becomes apparent when examining its sophisticated approach to identity-based security. In modern enterprises, managing identities extends far beyond human users to include services, applications, and infrastructure components. For instance, Starbucks utilizes HashiCorp Vault to secure secrets and manage identities for over 100,000 edge devices across its retail locations. This implementation ensures that both human and machine actors are authenticated and authorized securely, highlighting Vault's capability to handle complex identity-based security requirements.
For human authentication, Vault integrates seamlessly with enterprise identity providers through methods like OIDC, LDAP, and JWT. This integration enables organizations to maintain consistent access control policies while leveraging existing identity management investments. Vault Enterprise enhances these capabilities with Sentinel integration for Policy-as-Code, allowing organizations to implement sophisticated access control policies that consider factors such as time of day, IP address ranges, and MFA status.
Machine authentication in Vault represents a crucial capability for modern infrastructure. Through methods like Kubernetes authentication, cloud provider-specific auth methods, and TLS certificates, Vault enables secure machine-to-machine communication and automated access to security services. This capability is particularly valuable in dynamic environments where traditional IP-based security proves inadequate.
When combined with Consul for service discovery, network segmentation, and service mesh capabilities, and Terraform for infrastructure provisioning, Vault creates a comprehensive security foundation for modern application architectures.
Encryption-as-a-Service
Modern applications increasingly require encryption capabilities, yet implementing proper encryption remains challenging. Vault's Encryption-as-a-Service (EaaS) capabilities enable organizations to centralize and standardize their encryption operations through the Transit secrets engine. This service provides sophisticated encryption operations, including key rotation, data encryption/decryption, and secure key management.
The usage is straightforward: A person or an application authenticates itself and sends data—such as a document with sensitive information—to a REST API endpoint. Vault then encrypts the data as specified for this user or application and returns the encrypted document. This document can then be safely stored in a database, file system, CMS, or any other required location. The decryption process follows the same workflow: The encrypted document is sent to Vault, which returns the decrypted content.
The Transit engine supports various encryption algorithms and key types, enabling organizations to implement encryption that meets their specific security and compliance requirements. Key rotation can be automated based on time or number of uses, ensuring proper cryptographic hygiene without operational overhead. Through careful integration with applications and infrastructure, organizations can implement comprehensive encryption services that protect sensitive data while maintaining operational efficiency.
Enterprise PKI and Certificate Management
 Public Key Infrastructure (PKI) management represents one of Vault's most powerful capabilities. The PKI secrets engine enables organizations to implement sophisticated certificate management workflows, including automated certificate issuance, rotation, and revocation. This capability extends from simple SSL/TLS certificates to complex multi-tier PKI hierarchies that can support entire organizational security infrastructures.
Public Key Infrastructure (PKI) management represents one of Vault's most powerful capabilities. The PKI secrets engine enables organizations to implement sophisticated certificate management workflows, including automated certificate issuance, rotation, and revocation. This capability extends from simple SSL/TLS certificates to complex multi-tier PKI hierarchies that can support entire organizational security infrastructures.
In enterprise environments, Vault's PKI capabilities enable organizations to maintain complete control over their certificate lifecycle while ensuring proper security controls and audit capabilities.
A notable example is athenahealth, a leading healthcare technology company, which adopted HashiCorp Vault to streamline and standardize its secrets management operations. This move enhanced their security posture and ensured the protection of sensitive patient and operational records.
Root CAs can be stored offline or protected by HSMs, while intermediate CAs managed by Vault handle day-to-day certificate operations.
Integration with Terraform enables automated certificate provisioning as part of infrastructure deployment, while Consul integration enables automatic certificate distribution and rotation for service mesh implementations.
Integration with HashiCorp Tools and Enterprise Systems
Vault's integration capabilities extend beyond basic API access to include deep integration with other HashiCorp tools and enterprise systems. The combination of Vault, Terraform, and Consul enables sophisticated security automation and service mesh implementations. For example, Expedia leverages these tools to maintain a reliable compute platform for its customers, ensuring secure and efficient operations across its services.
Terraform can automate the deployment and configuration of Vault infrastructure, while Consul provides service discovery, network segmentation, and service mesh capabilities.
Through Terraform providers and custom integrations, organizations can automate the provisioning of secrets, certificates, and encryption services as part of their infrastructure deployment process. This integration enables security-as-code practices, where security configurations and policies are version-controlled and automatically applied across environments.
Addressing Critical Enterprise Security Requirements
Implementing Enterprise-Grade High Availability
High availability in security infrastructure is non-negotiable for enterprise environments. For example, Citi, a global financial services company, utilizes HashiCorp Vault to manage secrets and protect sensitive information across its vast infrastructure, ensuring high availability and robust security measures.
Any disruption in access to security services can result in widespread service outages. Vault Enterprise addresses this through its integrated Raft storage and sophisticated clustering capabilities. Performance Replication enables organizations to maintain multiple active Vault clusters across datacenters and regions, ensuring low-latency access to security services while meeting data sovereignty requirements.
The PKI infrastructure managed by Vault must be particularly resilient, as certificate operations are critical for ongoing system operations. Vault's architecture ensures that certificate issuance services remain available even during maintenance windows or partial system outages. However, there is one limitation: Vault itself does not provide a Certificate Revocation List (CRL) Distribution Point (CDP) or Online Certificate Status Protocol (OCSP) service. If CRL generation is interrupted due to downtime, dependent systems may not be able to check certificate revocation status.
The Transit secrets engine for encryption services is designed to maintain availability through cluster operations, ensuring that applications can consistently access encryption and decryption capabilities.
But as a seasoned IT decision-maker or experienced engineer, you know one thing for sure: Disaster will always strike in unexpected ways. HashiCorp Vault is no exception to this rule. Disaster recovery capabilities in Vault Enterprise provide additional resilience through dedicated DR replication clusters. These clusters maintain up-to-date copies of Vault's data and configuration, including PKI certificates, encryption keys, and authentication policies, enabling rapid failover in case of regional outages or other disasters. However, this resiliency does not equal self-healing—the implementation of DR clusters requires careful consideration of network connectivity, monitoring, and failover procedures to ensure business continuity.
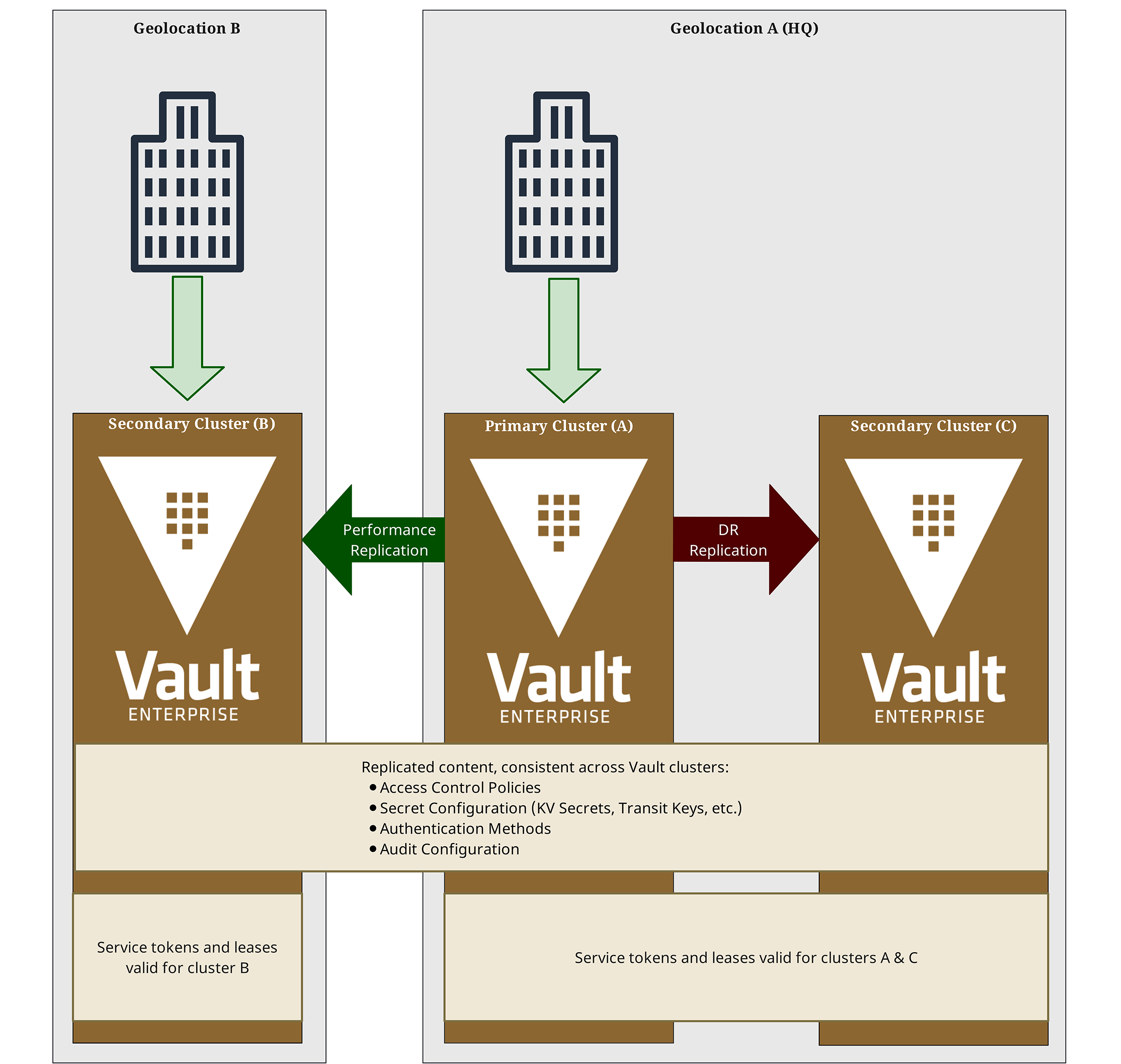
If multiple clusters are needed for performance reasons, for example because certain secrets are required in a different data center, a combination of DR replication with performance replication is recommended.
In the diagram shown, Cluster A (middle) replicates all data to Cluster B (left). This creates a 1:1 copy of the primary cluster in Cluster B, clients can connect to Cluster B. But their tokens and leases are only valid locally on Cluster B; an employee working in geolocation B can NOT automatically use their tokens to get access to the HQ infrastructure (or vice versa) without explicitly granted permissions and connecting to the Vault cluster in geolocation A.
For disaster recovery, Cluster A also replicates to a DR Cluster C. The service tokens are then valid on Clusters A and C (to allow switching in case of disaster) but not on Cluster B.
Ensuring Comprehensive Audit and Compliance
Compliance requirements in modern enterprises demand comprehensive audit capabilities and granular access controls. Vault Enterprise provides detailed audit logging of all operations, including:
- Successful and failed authentication attempts
- Secret access
- Certificate operations
- Encryption activities
- Configuration changes
These audit logs can be integrated with enterprise SIEM systems like Splunk or the ELK stack for centralized security monitoring and analysis.
For PKI operations, Vault maintains detailed records of certificate issuance, renewal, and revocation, enabling organizations to demonstrate compliance with standards like PCI DSS and SOX. The Transit engine's key rotation and encryption operations are similarly logged, providing a clear audit trail of cryptographic operations and key lifecycle events.
Sentinel integration in Vault Enterprise enables sophisticated policy enforcement that goes beyond basic access controls. Organizations can implement policies that enforce compliance requirements such as mandatory encryption, access time restrictions, and geographic limitations. These policies apply to both human and machine identities, ensuring consistent security controls across all types of access.
Sentinel policies can enforce specific requirements for certificate issuance, key usage, and encryption operations, ensuring that security operations align with organizational policies. By leveraging policy-as-code principles, organizations can enforce security compliance across all environments while maintaining flexibility in access control management.
Scaling Security Infrastructure Across the Enterprise
As organizations scale their use of Vault, proper architecture and operational procedures become crucial. Namespace isolation in Vault Enterprise enables organizations to maintain logical separation and isolation between different business units and applications while managing them through a single Vault infrastructure. This capability is particularly valuable for large enterprises that need to maintain separate security domains while ensuring consistent policy enforcement.
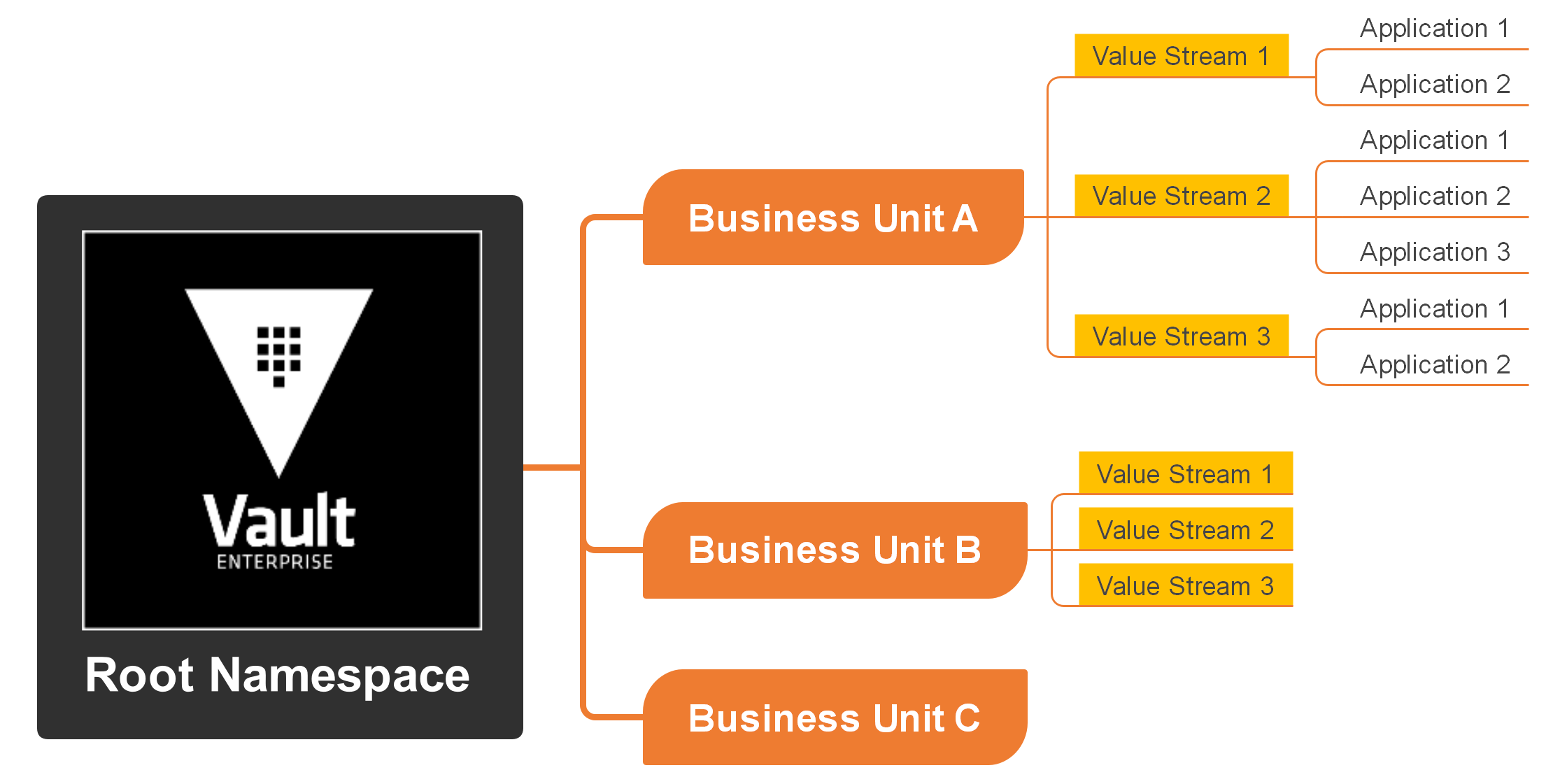
Each namespace can maintain its own PKI infrastructure, encryption keys, and authentication policies while inheriting enterprise-wide security controls. This approach enables organizations to delegate security management to individual teams while maintaining centralized oversight and compliance enforcement.
Control groups in Vault Enterprise provide additional governance capabilities by requiring multiple approvals for sensitive operations. This feature is particularly valuable for implementing separation of duties and ensuring proper oversight of critical security operations. Organizations can define sophisticated approval workflows for operations such as root certificate generation, master key rotation, and policy modifications, ensuring proper governance of critical security infrastructure.
The scale of machine authentication in modern enterprises requires careful consideration of performance and automation. Vault's architecture enables efficient machine authentication through mechanisms like automatic certificate renewal and batch token generation. Integration with Consul enables automatic distribution of certificates and security credentials to services, while Terraform automation ensures consistent security configurations across environments.
Looking Forward
As enterprise security requirements continue to evolve, the role of sophisticated security infrastructure in maintaining security and compliance becomes increasingly critical. Organizations must adopt comprehensive approaches that can handle the complexity of modern environments while ensuring consistent security controls across human and machine identities.
HashiCorp Vault’s comprehensive approach to security infrastructure, combined with the enterprise features available in Vault Enterprise, provides a robust foundation for addressing these challenges. By implementing proper architecture and leveraging advanced features for PKI, encryption services, and identity-based security, organizations can build resilient security infrastructure that meets their business needs while maintaining high standards for security.
The future of security infrastructure will likely see even greater emphasis on automation, zero trust architectures, and sophisticated machine identity management. Organizations that invest in building robust security capabilities today will be well-positioned to handle these evolving requirements while maintaining the security posture required in modern enterprise environments.